
Threat Hunting (or say TH) : Is proactive and rigorously looking after threats in estate.
So far we already some understanding of what is Threat Hunting!
How to establish a good Threat hunt according to SentinelOne:
- Ensuring right Data
- Clarity in Baseline To Understand What’s Normal In Environment
- Develop A Hypothesis Ideas can be derived from the following sources:
- MITRE ATT&CK framework: a vast knowledge base of attack tactics, techniques, and procedures. Studying the MITRE techniques and their simulation in test environments can serve as a foundation for developing hypotheses.
- Threat Intelligence reports: contain useful information about attack techniques and procedures based on real incidents. Systematic analysis of such reports should spark some thought and give rise to many threat hunting ideas.
- Blogs, Twitter, and conference talks: information about new attack techniques appears for the first time via research blogs, and conferences, even before the attackers start actively using it. The timely study of such information will allow threat hunters to be proactive and prepare before the new attack technique becomes widespread.
- Penetration testing: attackers tend to use tools similar to those applied by experienced pen testers. Therefore, studying pen-testing practices creates a treasure trove of knowledge for generating threat hunting hypotheses.
- Investigate & Analyze Potential Threats With Storyline, Deep Visibility returns full, contextualised data that lets you swiftly understand the root cause behind a threat with all of its context, relationships, and activities revealed from one search.
- Rapidly Respond To Remediate Threats (call for IR) Once you uncover a new TTP, you need to make sure you can effectively respond and remediate the threat. The response should distinctively define both short term and long term response measures that will be used to neutralise the attack.
- Enrich And Automate For Future Events Finally, successful hunts form the basis for informing and enriching automated analytics. This way, the organisation’s global security is enhanced thanks to the discoveries made during the investigation.
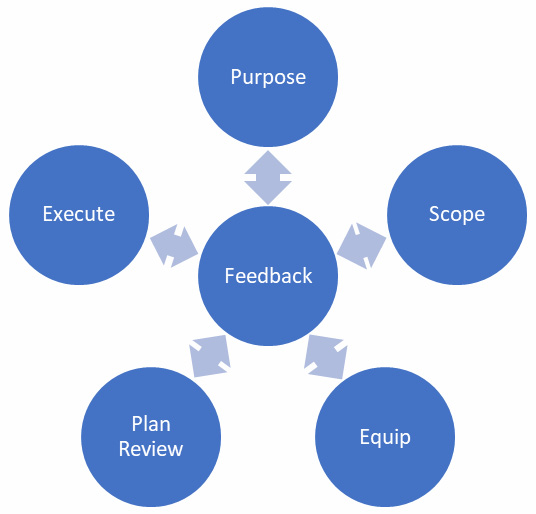
SANS Threat Hunting Model :
According to SANS, Threat hunting should be as 6 step cyclic model:
- Purpose – Define the objective of the hunt in alignment with organizational goals. Determine the necessary data sources and outline expected outcomes to ensure a focused and effective investigation.
- Scope – Develop a clear hypothesis and identify target networks, systems, or hosts for data collection. The scope should be broad enough to detect adversaries but refined enough to reduce unnecessary noise, ensuring a balanced and efficient hunt.
- Equip – Establish data collection and analysis methods, ensuring comprehensive coverage while minimizing biases. A Collection Management Framework (CMF) can be used to track data sources, improving visibility and consistency in analysis.
- Plan Review – Before execution, the team lead assesses the plan to ensure alignment with the organization’s security objectives. This step also verifies that all required resources—personnel, tools, data, and time—are in place for a successful hunt.
- Execute – Carry out the hunting process as per the approved plan, systematically analyzing data for signs of adversary activity while maintaining adaptability to pivot based on findings.
- Feedback – Evaluate results to refine future hunts. This step identifies potential biases, data gaps, and resource inefficiencies while improving detection strategies and enhancing overall hunting effectiveness.
Check this article below :
Threat Hunting vs. Threat Detecting: Two Approaches to Finding & Mitigating Threats
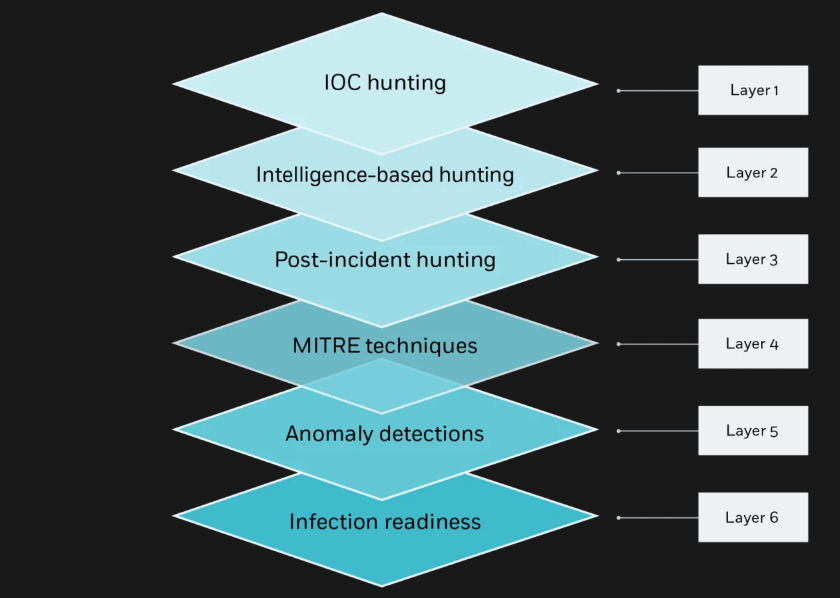
Hunting in Layers
- IOC hunting: Retro-hunts using IOCs –i.e., where known IOCs are queried across the multiple tools used by the SOC, including EDR, SIEM, Proxy, Firewall, and more.
- Intelligence-based hunting: Reports are gathered and recent threats, techniques, and unpatched vulnerabilities are searched for in the environment.
- Post-incident hunting: Leveraging the incident report from an event, workflows are used to identify additional backdoors or infected hosts.
- MITRE techniques: After mapping the environment, any MITRE TTP blind spots are used to create a customized, dedicated plan for a specific organization.
- Anomaly detection: A wealth of data is used to detect anomalies from a customized baseline, such as cryptomining, malware beaconing or unauthorized data transfer.
- Infection readiness: As no threat hunting process is airtight, this layer is about hardening response, deploying deception, and preparing response for attack.
Output of Threat Hunting :
Now Comes part where we assess our Threat Hunting program’s success SANS has designed model : Threat Hunting maturity Model
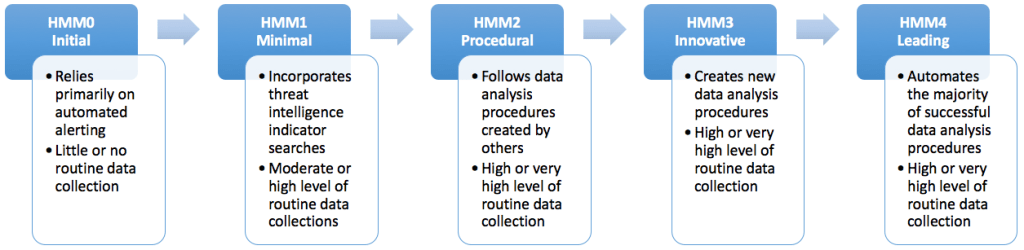
The initial and minimal levels heavily rely on automated detection tools, with some cyber threat intelligence at the initial level.
The procedural, innovative, and leading levels depend on extensive data collection, distinguishing them by the team’s ability to create custom data analysis procedures and avoid repetitive hunts.
HMM0 – Initial
Organizations at HMM0 depend entirely on automated detection tools like IDS, SIEM, or antivirus for threat detection. While they may integrate threat intelligence feeds or create custom signatures, their efforts focus solely on alert resolution. Minimal data collection limits their ability to conduct proactive threat hunting.
HMM1 – Minimal
At HMM1, organizations still rely on automated alerts but start incorporating routine data collection. They leverage threat intelligence to track emerging threats and retrospectively search for indicators in their historical data. While hunting is minimal, it marks the first step toward proactive detection.
HMM2 – Procedural
HMM2 organizations adopt established hunting procedures that combine specific data sources with analytical techniques to identify malicious activity. They collect substantial enterprise-wide data and apply structured methodologies, often relying on least-frequency analysis. However, they primarily use pre-existing frameworks rather than developing their own.
HMM3 – Innovative
Organizations at HMM3 go beyond predefined procedures, developing their own hunting methodologies. They leverage advanced analytics, including statistical modeling, data visualization, and machine learning, to create repeatable and well-documented detection techniques. However, scaling these processes remains a challenge without additional resources.
HMM4 – Leading
HMM4 organizations achieve full automation of successful hunting processes, freeing analysts to focus on refining existing techniques and developing new ones. This continuous improvement cycle strengthens their detection program and enhances resilience against adversaries.
Automation in HMM
While both HMM0 and HMM4 emphasize automation, the key difference lies in its purpose. HMM0 organizations rely passively on vendor-supplied or in-house detection tools, reacting only to alerts. In contrast, HMM4 organizations actively innovate, experiment with new hunting methods, and automate proven techniques, ensuring constant evolution in their threat detection capabilities.
Applications of Automation in Threat Hunting
ref: 1245
Automation can be applied to various aspects of threat hunting, including data collection, event analysis, and attribute identification. AI-driven systems can process vast amounts of data to identify threats, making threat intelligence more efficient and actionable. Additionally, automated threat hunting labs can be set up using methods such as DetectionLab and HELK to practice and develop hunting skills.
# Example of automated threat hunting using machine learning
import pandas as pd
from sklearn.ensemble import IsolationForest
# Load data data = pd.read_csv(‘threat_data.csv’)
# Train isolation forest model model = IsolationForest() model.fit(data) # Predict anomalies anomalies = model.predict(data)
Code sample generated by AI. Please double-check responses.
While automation can enhance threat hunting, it is not a replacement for human intelligence and expertise. According to, the hardest part about threat hunting is that you can never be sure whether you have succeeded, and automation alone cannot replace the human hunting activity. Therefore, it is essential to strike a balance between automation and human involvement in threat hunting.
Future of Automation in Threat Hunting ref: 12467
The future of automation in threat hunting looks promising, with advancements in AI and machine learning expected to further enhance the efficiency and effectiveness of threat detection and response. As noted in, generative AI could revolutionize cybersecurity operations and products, including threat hunting. However, it is crucial to address the challenges and limitations of automation in threat hunting to ensure its successful adoption.
To continue Go to : Practical Threat Hunting approach
