Detection Engineering :
Quickly identifying, qualifying, and mitigating potential security incidents is a top priority for security teams. Identifying potential security incidents quickly is a fairly complicated problem to solve. In general terms, security personnel need to be able to do the following:
- Collect events from assets that require protection, as well as assets that can indirectly impact them.
- Identify events that may indicate a security incident, ideally as soon as they happen.
- Understand the impact of the potential incident.
- Communicate the high-value details of the event to all relevant teams for investigation and mitigation.
- Receive feedback from investigative teams to determine how the whole process can be improved.
Each of these steps can be difficult to execute within small environments.
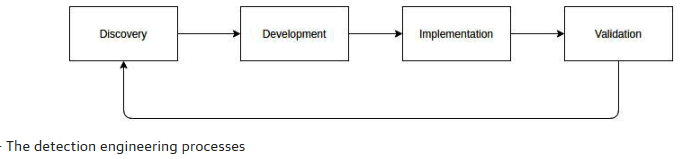
To accomplish these goals, a good detection engineering program typically needs to implement four main processes this is called as Detection Lifecycle:
- Discovery: This involves collecting detection requirements. Here, you must determine whether the requirements are met with existing detections. You must also determine the criticality of the detection, as well as the audiences and timeframes for alerting.
- Design, development, and testing: The detection requirement is interpreted, and a plan for implementing the detection is formulated. The designed detection is implemented first in a test environment and tested to ensure it produces the expected results.
- Implementation and post-implementation monitoring: Detection is implemented in the production detection environment. Here, the performance of the detection and the detection systems is monitored.
- Validation: Routine testing to determine the effectiveness of the detection engineering program as a whole:
The Differences between Threat Hunting v/s Detection Engineering v/s SOC Operations v/s Data Engieering
- Threat Hunting : The proactive establishment of investigative analyses by the threat hunting process is predicated on the assumption of a successful, undetected breach. Threats that are still active in the environment but have gotten past the security measures in place can be found using the threat hunting process.
- In Detectionm Engineering : Threat Hunting provides input to Detection ENgineering as it can identify what lacking in detection processes and infrastructure.These Deficiecies are solved by Detection Engineering.
- SOC Operation : It focues specifically monitoring the security estate and utlizes the security detection alerts which were been produces by The Detection Engineering team,.
- Detectionm Engieerning provides input to SOC teams and exctracts feedback on the rules that have created to minimize false positives in environment and incerase the quality of security detections and alerts.
- Data Engineering : The process of design, implement, and maintain systems to collect, transform, and distribute data, generally to fulfil data analytics and business intelligence mandates.
- Detection Engineering is shares simislar process and goals like data engineering however the data is strictly deals in cybersecurity.
What qualifies a Effieicent Detection Engineering Program for Entreprise ?
- The ability (set of mechanisms / processes) to detect the adversary : This involves attack surface Area coverage with the ability which can be mapped out on MITRE Attack Framework. The more effiecient way of dealing the vast widelands of MITRE is to create such detection rule which can cover more than one MITRE techniques with keeping in mind that it should also being lazer focussed not to generate noise / false positive.Hence increasing the durability of detection.
- The cost inccured / operational cost involved to support that Ability : The costs involve creation, running and maintaince of detections the resouces that were involved in revieiwong the alert (SOC teams or Dedidcated staff) and actions taken based on those alerts.
- Creation Time : Total time involed in process to decent working rule with relevance.
- Complexity: of the detection affects future analysts’ abilities to understand and maintain the detection
- Relevance to modern (present day) attack vectors adn techniques which also work hand in hand with Creation time as it every week there new attack vectors are launced one more sophosticated than previous.
- The cost to the Adversary to evade that Detection:the specific expenses related to carrying out an attack, we can use indirect evidence to calculate the adversary cost. Ranking the cost to the adversary can be aided by inherent knowledge of how simple it is for them to avoid detection, such as by consulting the Pyramid of Pain.
- Increasing the quality of alerts / reducing “analyst fatigue” : This happens when each alert reviewed by the Analyst and measured on 3 main parameters :
- Confidence of Alert : This can be measured in percentage as the probablity of triggered alert is a true positive.
- Noisiness of alert : how frequently the alert is been triggere this can been fixed by either breaking alert which broad logic adn picking up or regrouping of logic among various detection rules which matches the criterion and classification.
- Impact of alert : this is measure of severity of alert.
- Actionability of alert : this is the measure of how easy is it for the analyst to take action on the alert and remediate it with defined coarse of action.
- Specificity of alert : This supports the actionability of the alert by clearly mentioning what has been detected and why the alert is created. This could be sometimes also depends on Analyst competencies and ease of investigation.
All of factors when kept in consideration could exponetionally increase the Quality of Cybersecurity of the organisation. This could be worked via simple steps as time as deciding fixed times in week which would be dedicated for improving the detection of attacks vectors across estate by refining the detection rules on these parameters.
In next blog we will be discussing these steps in more detail.
Stay Tuned
