Welcome to the realm of cyber threat detection! When looking through a company’s digital estate as a threat hunter, one must be proactive and iterative in order to find and isolate numerous threats that bypass already installed security measures. Threat hunting is predicated on the idea that hackers have already gotten past the system’s perimeter protections and are hiding there covertly. In-depth discussion of the threat hunting process and how artificial intelligence has emerged as a key technology to alleviate the cybersecurity skills gap will be covered in this post.
The majority of threat hunts begin with an idea or an anomaly. The important thing is that we do not yet know whether or not our hypothesis is true, whether it be a narrowly focused or a broad and general one. Embracing this ambiguity and looking for evidence to support or refute our theories is the goal of threat hunting. As an alternative, beginning the threat hunt with anomaly detection, which identifies anomalous behavior in the system, can be successful. Hackers constantly strive to blend into the system to avoid detection, but there is always some element of abnormal behavior that can be picked up, such as repeated connections to strange external IP addresses or administrator credentials being stolen and used to authenticate against devices it has never interacted with before.
Once we have our hypothesis or anomaly, we need to collect data from endpoints, logs, and network data.Endpoint collection and log collection can require a lot of resources because they require a variety of sensors and frequently have gaps in coverage. On the other hand, network data is a fantastic resource for threat hunting. Data collection can be done more quickly and easily by mirroring network traffic from neuralgic points. Compared to gathering logs or installing endpoint agents, rolling out network sensors is less difficult, and once an event of interest has been identified, network data gives analysts situational awareness.
The threat hunter must analyze the data points, draw an interpretation, and decide whether the event proves the hypothesis to be correct or incorrect in the process’s final step. Investigating the data, examining it, and then drawing a conclusion are all parts of the process.
However, there is a severe lack of cybersecurity professionals with the necessary skills. Security teams work around-the-clock to defend systems that are under attack more frequently than ever before, and human threat hunters are in high demand. Since security personnel teams cannot be expected to keep up with the speed, scale, and sophistication of contemporary machine-powered attacks, artificial intelligence has emerged as a crucial technology.
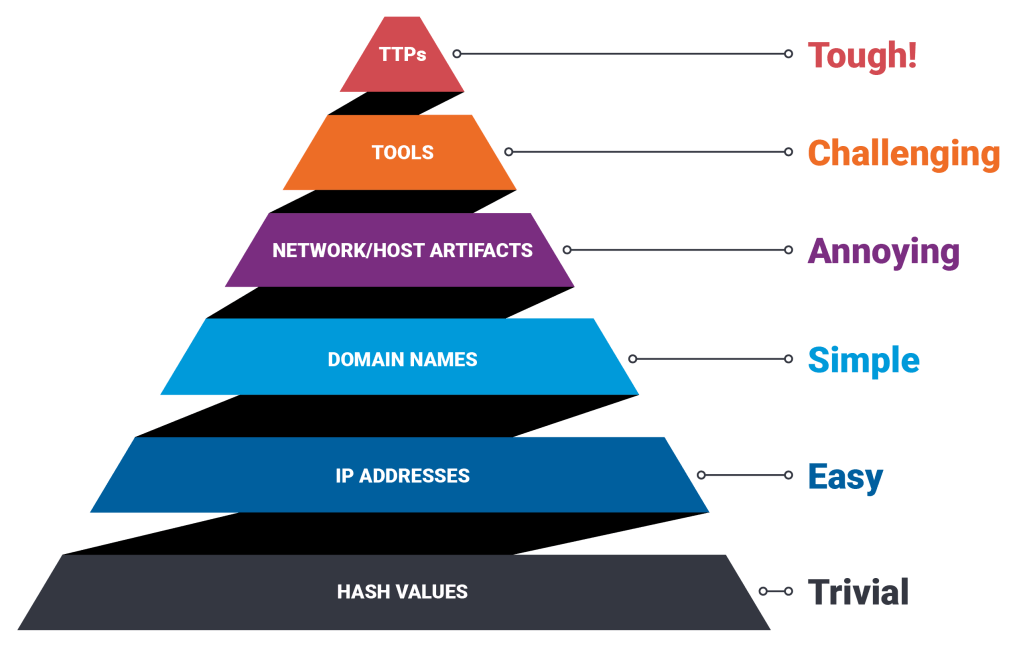
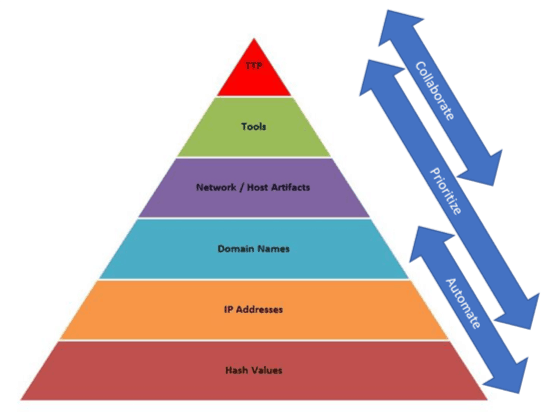
The various kinds of indicators of compromise (IOCs) are displayed in the pyramid of pain. Attackers find it extremely difficult to alter the components at the top of the pyramid, such as tools and TTPs (tactics, techniques, and procedures). While responding to IOCs at the bottom of the pyramid is only a hassle for online attackers, responding to those at the top of the pyramid makes life for hackers pretty miserable. A sizable portion of the pyramid can be covered by machine learning. Up to the TTPs, which can be understood and intelligently addressed in real-time by cyber AI technologies, AI technology can be used to identify indicators across this pyramid.